If you have been following banking, investing, or cryptocurrency over the last ten years, you may have heard the term “blockchain”, the record-keeping technology behind the Bitcoin network.
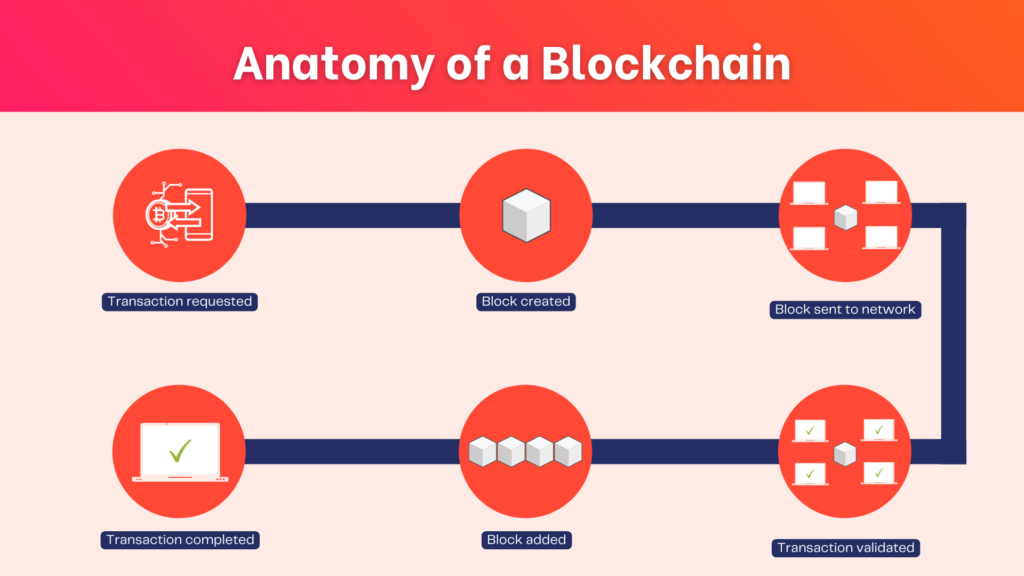
A blockchain is a specific type of database that differs from typical databases in the way it stores information. Blockchains store data in blocks that are then chained together.
As new data comes in, it is entered into a fresh block. Once the block has been filled with data, it is chained into the previous block, allowing the data to be chained together in chronological order.
Different types of information can be stored on a blockchain but the most common use, so far, has been a ledger for transactions.
In Bitcoin’s case, the blockchain is used in a decentralised way, so that no single person or group has control. Rather, all users collectively retain control.
Decentralised blockchains are immutable, which means that the data entered is irreversible. For Bitcoin, this means that transactions are permanently recorded and viewable to anyone.
What Are Some Advantages of Blockchains?
- They’re global: Cryptocurrencies can be sent across the world, quickly and cheaply.
- They increase privacy: Cryptocurrency payments don’t require you to include your personal information, which protects you from being hacked or having your identity stolen.
- They’re open: Every single transaction on cryptocurrency networks is published publicly in the form of the blockchain, so anyone can scrutinise them. That leaves no room for manipulation of transactions, changing the money supply, or adjusting the rules mid-game. The software that constitutes the core of these currencies is free and open-source so anyone can review the code.
Is Blockchain Secure?
Blockchain technology accounts for the issues of security and trust in several ways.
First, new blocks are always stored linearly and chronologically. That is, they are always added to the “end” of the blockchain. If you take a look at Bitcoin’s blockchain, you’ll see that each block has a position on the chain, called a “height.” As of March 2022, the block’s height has reached 727,528.
After a block has been added to the end of the blockchain, it is very difficult to go back and alter the contents of the block unless the majority reached a consensus to do so. That’s because each block contains its own hash, along with the hash of the block before it, as well as the previously mentioned time stamp.
Hash codes are created by a math function that turns digital information into a string of numbers and letters. If that information is edited in any way, the hash code changes as well.
Here’s why that’s important to security: let’s say a hacker wants to alter the blockchain and steal Bitcoin from everyone else. If they were to alter their own single copy, it would no longer align with everyone else’s copy. When everyone else cross-references their copies against each other, they would see this one copy stand out. That hacker’s version of the chain would be cast away as illegitimate.
Succeeding with such a hack would require that the hacker simultaneously control and alter 51% of the copies of the blockchain. Their new copy becomes the majority copy and thus, the agreed-upon chain. Such an attack would also require an immense amount of money and resources. All of the blocks would need a redo, as they would have different timestamps and hash codes.
Due to the size of Bitcoin’s network and how fast it is growing, the cost to pull off such a feat would probably be insurmountable. Not only would this be extremely expensive, but it would also likely be fruitless. Doing such a thing would not go unnoticed, as network members would see such drastic alterations to the blockchain. The network members would then fork off to a new version of the chain that has not been affected.
This would cause the attacked version of Bitcoin to plummet in value, making the attack ultimately pointless as the bad actor has control of a worthless asset. The same would occur if the bad actor were to attack the new fork of Bitcoin. It is built this way so that taking part in the network is far more economically incentivised than attacking it.





